

jka
-
Posts
244 -
Joined
-
Last visited
Posts posted by jka
-
-
Thanks BSmither,
Yes, we want it to be the same behavior as a successful transaction . Will add this line of code and check what shakes out. The "To Review" is really a Credit Card status for the merchant. To the user/purchaser the order has been received. If the merchant goes to the Fraud Detection Suite and sees that its a questionable transaction, then the merchant can always cancel the order.
The problem is more to do with the user still sitting on the credit card input page.
-
I had posted to an existing thread last week. Today I submitted an order in the system on behalf of my customer. the result received from Authorize.net is 4|1|253
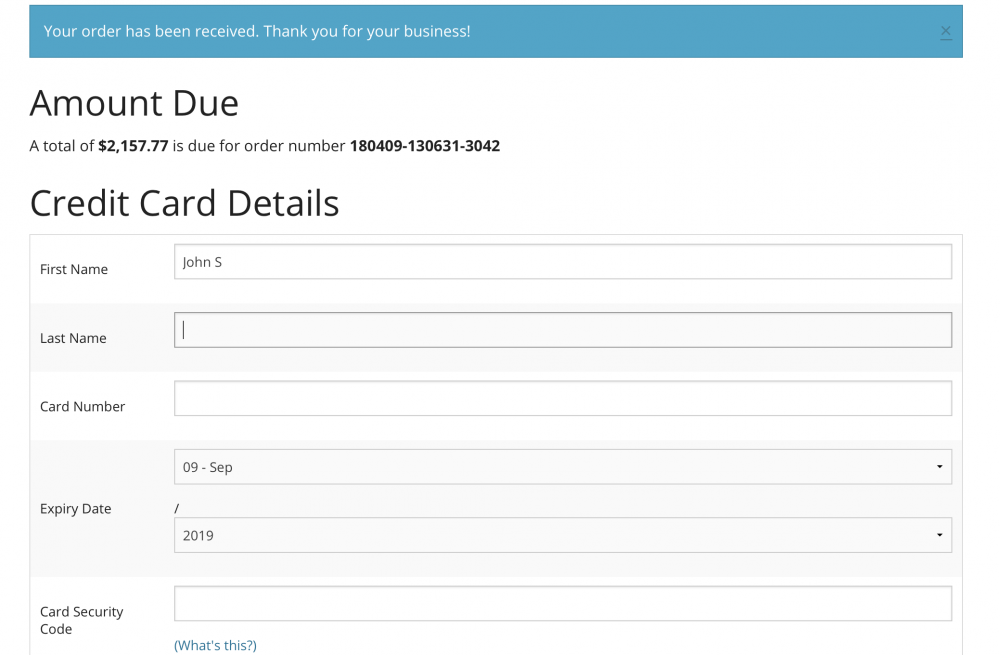
bSmither had given us a fix for 1.3 version and then Al had updated to 1.4 with fixes. Since then, the behavior is not as expected. Please see screenshot attached. It shows order received but still still on the credit card form page.
How can we mimic the same behavior as 1|1|1 for 4|1|253
-
We have updated to 1.1.4 for the last couple of months. The status from AIM with "4 1 253" works fine now with the custom message from Authorize.net.
However here is the issue, unlike when the status is "1" where its gets redirected to a Order Complete page, in this case of "4", it displays the message properly etc adds to pending order. However it still sits on the credit card form page. Customers that get a "4" (Fraud Detection Suite) from Authorize, get the order received in pending status on the screen with the CC form below. They end up entering the card info again and sometimes we get 2-3 authorizations.
How can change the behavior of "4" similar to "1" and take them away from the CC input screen.
On 11/21/2017 at 6:26 AM, Al Brookbanks said:Thanks so much. I removed some comments and published it in 1.1.4.
-
SSL Version NSS/3.28.4
-
The AIM method stopped working since this past weekend. When we contacted Authorize.net they say its probably related to disabling TLS 1.0 and 1.1. We had this issues with UPS module and have the latest cURL ... curl --version
curl 7.57.0 (x86_64-redhat-linux-gnu) libcurl/7.57.0 NSS/3.28.4 zlib/1.2.7 libpsl/0.7.0 (+libicu/50.1.2) libssh2/1.8.0 nghttp2/1.21.1
Release-Date: 2017-11-29In the transaction logs its a cURL timeout
cURL Error (28): Connection timed out after 15000 milliseconds
The UPS module started working fine once we updated cURL and we have also disable TLS1.0 and 1.1
Any hardcoding on the Authorize.net module??
-
Hello Bsmither,
I tried a few other random numbers but somehow 23 seemed invoke that coupon. We disabled that coupon for now. Not sure if there are others. Any nibbles on what you found or to fix?
-
A good customer called this morning and pointed an issue on the website. So, by default the store calculates Tax before checkout. This customer tried to put in a negative $$ value of the tax in the coupon code box. Say $23 in the coupon section. This brought him a discount from an existing coupon from 2 yrs back (which was still active) and gave him a big discount. The displayed coupon is a Alphanumeric coupon and not sure how entering 23 into the coupon code invoked that coupon??
How do we fix this? Not sure if just entering a random numeric number by the customer brings out previous coupons or even current ones.
Thanks.
-
Thanks BSmither. I will take a look at it. I have purchased a few of the shipping modules in the past and its probably one of them.
-
We have the Free Shipping extension configured and in the process, we removed HI and AK from United States Zones. Now on the flip side, a customer from HI is not able to get shipping rates as HI missing from the list of states in the drop-down. Any pointers in fixing this without impacting free shipping.
-
Absolutely. I also went ahead and updated to the latest OpenSSL version too. We all assumed that updating php takes care of cURL but obviously not the case. In fact we had to download the cURL libraries independently of Plesk. The normal Yum stuff didnt work.
-
Thanks. The server is PCI-DSS compliant with only TLS1.2 permitted by the webserver as well as A+ result from SSLlabs test. The cURL libraries are not part of Plesk and hence it wasnt on the radar whenever the server is automatically updated.
-
We went ahead and did a cURL library update to the latest version 7.57 and its fixed now. Everything is back up and running. Thanks.
-
BSmither,
Just the user.class? not the cubecart.class?
-
BSmither et-all.
We are on 6.1.12, however would like to address the security issue with database class php. Can we just copy that file alone from 6.1.13 and patch it into 6.1.12?
-
We have our own Plesk VPS server for Production and a separate one for QA. I have added enough info for Noodleman to t-shoot the module. It appears that UPS were moving away from their legacy tools since 2017 and they decided to pull the plug Jan 1. As of now they are throttling their legacy API calls and the reason for the intermittency.
https://www.ups.com/us/en/help-center/technology-support/data-security.page
-
We just went ahead and made only TLSv1.2 as the only available TLS on the server. This way all transactions from the server will be 100% TLS 1.2. However the issue still remains. Hopefully Noodleman will have the fix tomorrow.
-
You were spot on, it seems that module does not use the Request.class. There is still nothing in the log after the change.
-
So, the UPS_contract module stores it error logs in the module window. There is nothing in the request.log for UPS Contract. However I added the standard UPS module and noticed in the request.log that it calls http://ups.com/xxxxx
Maybe we can try temporarily patching up http://ups to be forced as https://ups until the developer takes a look and patches it up.
-
Unfortunately that wasn't the issue. Its probably something to do with the url change.
-
Just checked shipping.class.php and admin, its all encoded gibberish. Will have to wait for the Noodleman to respond since the url change at UPS seems to causing this issue.
I am surprised that others have not reported this yet.
-
Hello BSmither,
Happy New Year !
I see the following ..
Registered Stream Socket Transports tcp, udp, unix, udg, ssl, sslv3, sslv2, tls, tlsv1.0, tlsv1.1, tlsv1.2
I wonder if the module is using TLS to make the calls explicitly?? We use UPS Contract. For now due to this issue, we are dead in the water since the cart does not let checkout without proper shipping rates.
Here is the response from UPS ...
UPS has upgraded the communication security protocols for all web-based applications, including UPS Developer Kit, UPS.com, CampusShip, and etcetera. Please contact your company's IT department or development team to ensure that any security protocols currently used meet the TLS 1.2 requirement. If Java is enabled, it must be version 1.7 or higher to use TLS 1.2.
As of December 31, 2017, all API URLs, including old API URLs starting with www.ups.com/ups.app/xml/ or https://www.ups.com/webservices/, have been transitioned over to ignore any traffic using TLS 1.0.
If you are using any API URLs starting with www.ups.com/ups.app/xml/ or https://www.ups.com/webservices/, please update them to the currently supported URLs noted in their respective Developer Guides. They start with https://www.onlinetools.com.
Please note that our CIE Environment will only accept TLS 1.2 requests since it was transitioned over back in February 2017.
-
Just called UPS and they said as of today if the website is not using TLS 1.1 or 1.2 they are rejecting 75% of legacy tools.
Any pointers on this TLS 1.1 or 1.2 ???
-
Actually its very intermittent and shows one rate at a time or shows error everytime we reload the screen. This prevents the customer from being able to checkout.
-
Folks, Anyone having issues since Jan 1 with the UPS Contract module? It doesnt seem to be fetching any rates, I get the big red error box which states no suitable shipping methods found.

Paypal Payflow Link
in Extension Discussion
Posted
The existing PayFlow Link extension does not work. We will be willing to pay for the development or enhancement of the existing extension or a new one.
The Payflow link extension should support "Transparent ReDirect".
1. Info: https://www.paypalobjects.com/webstatic/en_US/developer/docs/pdf/paypal_transparent_redirect.pdf
2. Examples flow of hosted flow logic
https://developer.paypal.com/docs/classic/payflow/integration-guide/#configuring-hosted-checkout-pages